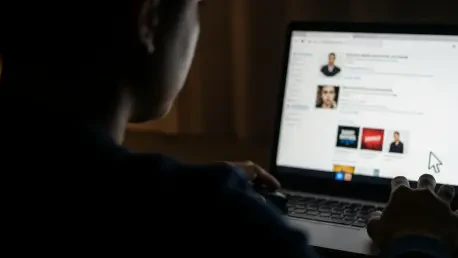
A meticulously crafted story about a celebrated national hero’s fall from grace recently captivated online audiences, but the viral scandal surrounding a supposed Filipino gold medalist was nothing more than a sophisticated trap designed to exploit human curiosity for malicious data theft. The elaborate hoax, which centered on a fabricated controversy involving a non-existent Olympic athlete, serves as a stark case study in how disinformation campaigns are weaponized to harvest sensitive user information. By hijacking the public’s fascination with scandal and celebrity, cybercriminals have demonstrated a potent new formula for turning viral content into a delivery system for malware and phishing schemes. This incident underscores a disturbing trend where the line between reality and digital fiction is purposefully blurred, not just for political gain or social disruption, but as a direct pipeline to a user’s digital life, transforming a click driven by morbid curiosity into an irreversible security breach. The campaign’s success reveals a critical vulnerability not in our software, but in our psychology, showing how easily our collective attention can be manipulated and monetized by those with nefarious intent.
The Anatomy of a Digital Deception
Crafting a Fabricated Persona
The entire disinformation campaign was built upon a foundation of identity theft, targeting a digital content creator named Zyan Cabrera, known online as Jerriel Cry4zee, who was falsely presented as a gold medalist from the 2026 Winter Olympics. This narrative was a complete fabrication; Cabrera is not an athlete and has no connection to the Olympic Games. The scammers constructed a “Frankenstein” persona by taking a single, decontextualized photograph of her wearing a medal from a minor local event and skillfully grafting this image onto the high-volume search traffic associated with the international sporting event. This strategy allowed them to create a believable, yet entirely false, story of a celebrated hero embroiled in a scandal. The selection of Cabrera highlights a significant shift in targeting tactics by malicious actors. It demonstrates that fame is no longer a prerequisite for becoming the centerpiece of a digital attack; mere visibility is sufficient. By leveraging an existing online presence, however modest, scammers can build a plausible backstory that withstands initial scrutiny, making the subsequent hoax far more effective at luring in unsuspecting victims who are quick to believe the dramatic downfall of a public figure.
The Lure of Manufactured Scandal
This operation functions as a textbook example of “SEO poisoning,” a technique where cybercriminals contaminate search engine results to push malicious sites to the top. The campaign’s timing was not accidental; it was meticulously synchronized to coincide with the heightened public interest and search traffic generated by the Winter Games. Malicious actors seeded social media platforms, particularly Facebook and Telegram, with provocative posts and links promising access to a scandalous video that allegedly led to the athlete’s downfall. However, the true danger was never in the non-existent footage but in the malicious links themselves. These URLs were designed to redirect users into one of two primary digital traps. The first was a sophisticated phishing scheme involving a nearly identical replica of the Facebook login page, engineered to harvest user credentials. The second, more insidious trap, prompted users to download a “special video codec” required to view the content. This file was not a codec but a potent form of spyware designed to infiltrate the user’s device and steal sensitive data, including personal files and critical banking information, turning a moment of voyeuristic interest into a significant personal security crisis.
The Technological Arsenal Behind the Attack
AI as a Tool for Character Assassination
A crucial element in the hoax’s success was the sophisticated use of artificial intelligence to lend credibility to the fabricated scandal. The perpetrators deployed AI-powered editing tools to manipulate innocent video clips of Zyan Cabrera, seamlessly splicing them with AI-generated or unrelated explicit material to create compelling thumbnails and short teaser clips. These visuals were specifically engineered to pique morbid curiosity while cleverly circumventing the content moderation filters on major social media platforms. By generating content that was algorithmically ambiguous, the scammers ensured their posts remained online long enough to achieve viral spread. This technique of digital character assassination represents a disturbing and growing trend in cybercrime. A similar methodology was previously observed in scams targeting other online personalities, such as the one involving Vera Hill, indicating that this is becoming a standard tactic. The low cost and increasing accessibility of AI tools mean that creating deepfakes and other forms of synthetic media is no longer the exclusive domain of state-sponsored actors, empowering smaller criminal groups to launch highly effective and damaging disinformation campaigns.
The True Victims of Voyeurism
Ultimately, this elaborate campaign weaponizes the very human trait of voyeurism against the public. The “Pinay Gold Medalist” saga serves as a powerful illustration of how easily reality can be distorted and weaponized in the modern digital ecosystem. The core finding from this event is that when users click on a link promising to expose the private shame or misfortune of another person, they are unwittingly exposing themselves to far greater personal risks. The individuals who sought to view the non-existent scandalous video became the true victims, voluntarily walking into a digital ambush that resulted in the theft of their personal credentials, financial data, and other sensitive information. This dynamic fundamentally reframes the nature of such scams; the target of the slander is merely the bait, while the audience, driven by a desire to witness a downfall, becomes the actual prey. The operation’s success depended not on a technical vulnerability in a system but on a psychological one in its users, proving that the most effective exploits are often those that target human nature itself.
A Reflection on Digital Trust
The incident involving the fabricated gold medalist served as a critical reminder of the fragility of information in the digital age. It highlighted how threat actors had successfully manipulated public emotion and curiosity, turning a non-existent event into a potent tool for widespread data theft. The campaign’s design exposed a methodical understanding of social media dynamics, leveraging viral mechanics and search engine optimization to maximize its reach. The aftermath prompted a necessary re-evaluation of online verification habits, as the public contended with the realization that even seemingly credible stories, amplified by thousands of shares and comments, could be hollow fabrications. The event was not merely a technical failure but a social one, demonstrating that the most robust cybersecurity measures were often bypassed by exploiting the human element.